Understanding SSH ED25519 Keys: A Comprehensive Guide
ED25519 SSH keys offer superior security and performance compared to RSA. This guide explains why ED25519 is the better choice and provides a step-by-step tutorial on generating and using ED25519 keys for password-less authentication. Learn how to improve your SSH security today!
SSH keys are a cornerstone of secure, password-less authentication for remote servers. While RSA has been a widely used algorithm for SSH keys, the ED25519 algorithm has gained popularity due to its superior security and performance. This guide will delve into why ED25519 is a better choice than RSA and provide a step-by-step tutorial on how to generate and use ED25519 keys.
Why Choose ED25519 Over RSA?
1. Stronger Security with Smaller Keys
ED25519 provides a high level of security with a much smaller key size (256 bits) compared to RSA, which typically uses 2048 or 4096 bits. Despite the smaller size, ED25519 keys offer equivalent or stronger security due to the elliptic curve cryptography it employs. This makes ED25519 more resistant to certain types of cryptographic attacks, such as those potentially enabled by future quantum computing advances.
2. Faster Performance
ED25519 is optimized for speed, offering faster key generation, signing, and verification processes compared to RSA. This is particularly beneficial in environments where speed and efficiency are critical, such as in automated systems or large-scale deployments.
- Key Generation: ED25519 key pairs are generated significantly faster than RSA keys.
- Signing and Verification: Operations involving ED25519 keys are quicker, which can enhance the performance of systems that require frequent authentication.
3. Simplified Security Model
Unlike RSA, which supports a range of key sizes and configurations, ED25519 uses a single, fixed elliptic curve. This reduces complexity in both implementation and configuration, minimizing the risk of misconfigurations that could lead to vulnerabilities.
4. Smaller Key Size
The smaller key size of ED25519 not only improves security but also reduces the overhead in storage and transmission. This is particularly useful in constrained environments, such as embedded systems or when transmitting keys over limited bandwidth connections.
Quick Start: Using ED25519 for SSH
Now that we understand the benefits of ED25519, let's dive into how to generate and use these keys for SSH authentication.
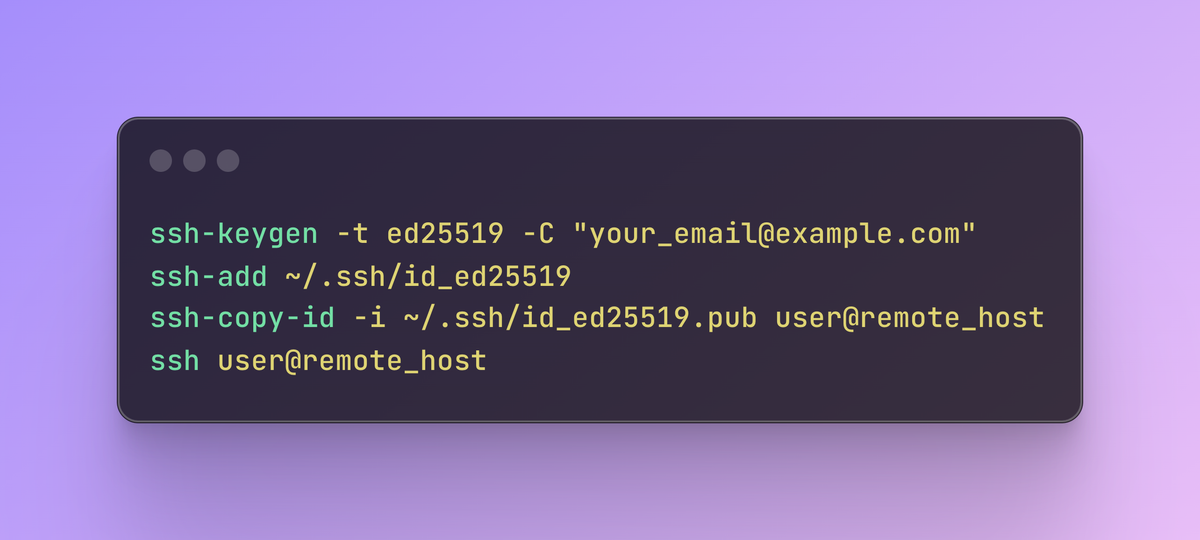
Step 1: Generate an ED25519 Key Pair
To generate an ED25519 key pair, open your terminal and run the following command:
ssh-keygen -t ed25519 -C "your_email@example.com"
- The
-t ed25519flag specifies that you want to use the ED25519 algorithm. - The
-C "your_email@example.com"option adds a comment to your key, which is helpful for identifying it later.
You will be prompted to choose a file location for the key. The default location (~/.ssh/id_ed25519) is usually fine, but you can specify a different path if needed. Optionally, you can set a passphrase for added security. If you do, you'll need to enter this passphrase whenever you use the key.
Step 2: Add Your SSH Key to the SSH Agent
Adding your key to the SSH agent allows your SSH client to use it automatically, without prompting for the passphrase every time. To add your key, use the following command:
ssh-add ~/.ssh/id_ed25519
If you chose a custom file location in the previous step, replace ~/.ssh/id_ed25519 with the correct path.
Step 3: Copy the Public Key to the Server
To use your new ED25519 key for SSH authentication, you'll need to copy the public key to the remote server. This can be done with the ssh-copy-id command:
ssh-copy-id -i ~/.ssh/id_ed25519.pub user@remote_host
- Replace
userwith your username on the remote server. - Replace
remote_hostwith the IP address or hostname of the server.
The ssh-copy-id command appends your public key to the ~/.ssh/authorized_keys file on the remote server, allowing you to authenticate without a password.
Step 4: Connect to the Server
With the public key installed on the server, you can now connect using SSH without needing to enter a password:
ssh user@remote_host
If your SSH key is correctly configured, you'll be logged in without further prompts.
Managing and Troubleshooting SSH Keys
Managing Multiple SSH Keys
If you manage multiple servers or use different SSH keys for different purposes, you can specify which key to use in your SSH configuration file (~/.ssh/config). Here's an example configuration:
Host server1
HostName 192.168.1.100
User your_username
IdentityFile ~/.ssh/id_ed25519
Host server2
HostName 192.168.1.101
User your_username
IdentityFile ~/.ssh/id_ed25519_other
This configuration file allows you to easily manage multiple SSH connections with different keys.
Troubleshooting SSH Authentication Issues
If you encounter issues when connecting to a server using your ED25519 key, here are a few troubleshooting tips:
- Check Key Permissions: Ensure your private key (
~/.ssh/id_ed25519) has the correct permissions. It should be readable only by you (chmod 600 ~/.ssh/id_ed25519). - Verify Key Installation: Ensure the public key is correctly installed on the server by checking the
~/.ssh/authorized_keysfile. - SSH Agent: Ensure your key is loaded into the SSH agent using
ssh-add -lto list the loaded keys. If it's not listed, add it usingssh-add ~/.ssh/id_ed25519.
Rotating SSH Keys
For security, it's a good practice to periodically rotate your SSH keys. This involves generating a new key pair and replacing the old public key on all remote servers where it's used. Here's a quick guide to rotating your keys:
- Generate a New Key Pair: Follow the steps above to create a new ED25519 key pair.
- Add the New Public Key to Servers: Use
ssh-copy-idto add your new public key to each server. - Test the New Key: Before removing the old key, test the new key by connecting to each server.
- Remove the Old Key: Once the new key is confirmed working, remove the old key from the
authorized_keysfile on each server.
Conclusion
ED25519 is a modern, efficient, and secure alternative to RSA for SSH keys. With its advantages in security, performance, and simplicity, it is an excellent choice for anyone looking to enhance their SSH security practices. By following the steps outlined in this guide, you can easily transition to using ED25519 keys and enjoy the benefits of this advanced cryptographic algorithm.
Remember, security is an ongoing process. Regularly review and update your SSH practices to stay ahead of potential threats.